Hack The Box: Horizontall(Linux)
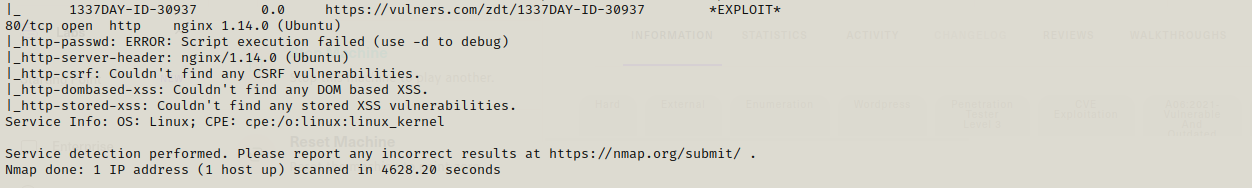
Lets start with an nmap scan
Although there are multiple vulnerabilities in ssh but then if port 80 is given that should be the first thing we explore.
We need to add horizontall.htb in our /etc/hosts file with the ip address of the website ,so that it works. After that we just need to type the ip address in our browser.
This web page has nothing, even the buttons are of no use. So the next thing should be directory busting but that leads us nowhere. We need to rather find the subdomains.
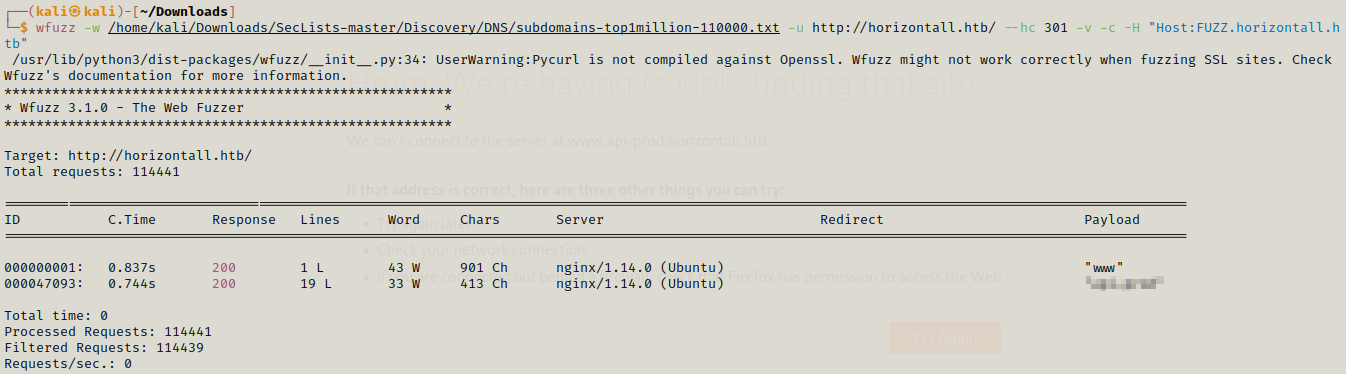
We found one subdomain and going there shows us nothing but a text .
We only know its an API , so we do directory busting on this.
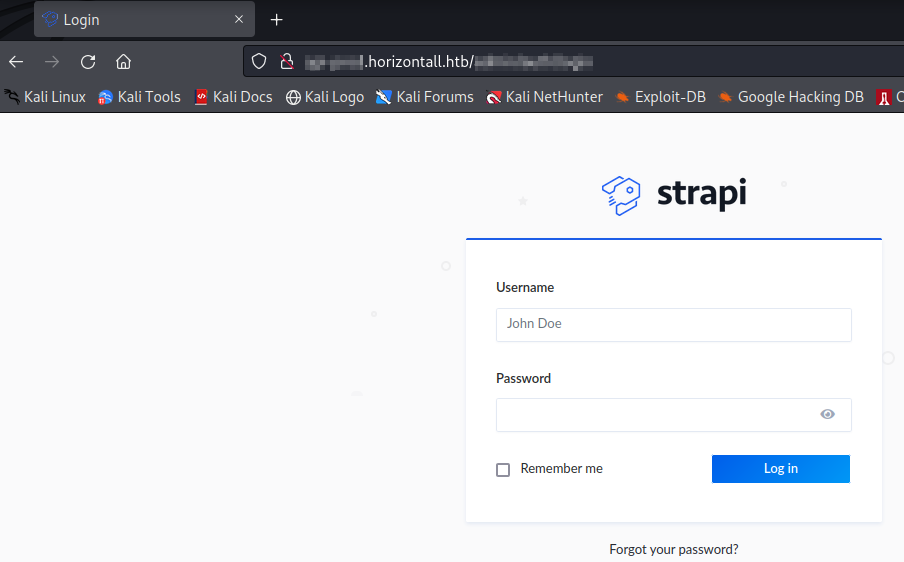
Now here we found a couple of pages but one of the page stands out which is a login page.
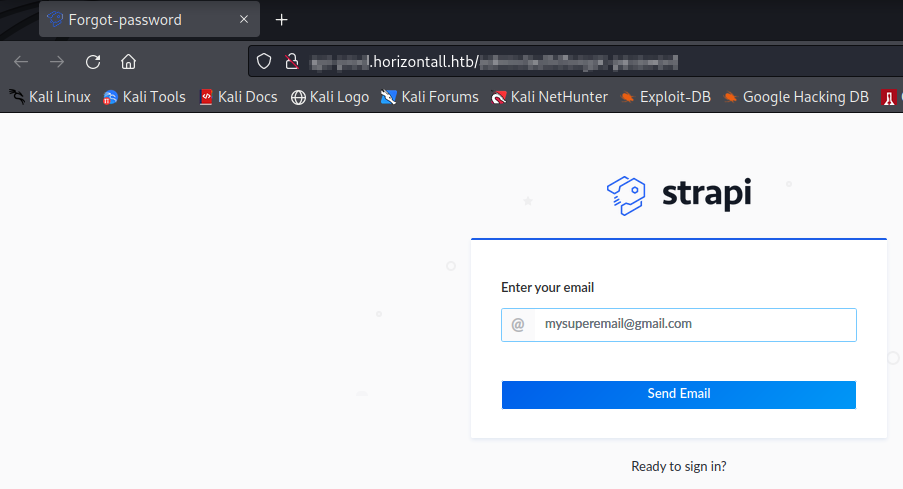
We can try the default username and password for strapi which are admin:admin but they don’t work. Even for forgot password we need email and we don’t have any information regarding that.
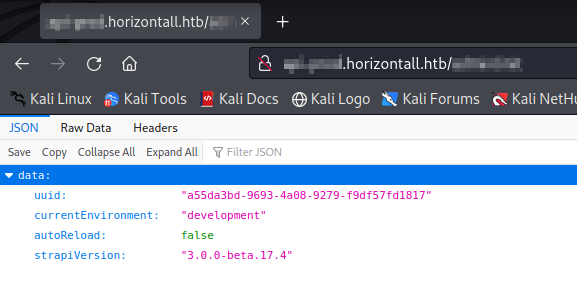
But there is one directory which gives us idea about strapi version.
This directory was not listed in dirb result but we can search exploit about strapi and the exploit which will be useful later on had this in its code. Another way of finding the version is to look for the js file of the login page and there we can find the version of strapi.
Now that we know the version the exploit for strapi can be used .It is a remote code execution exploit.
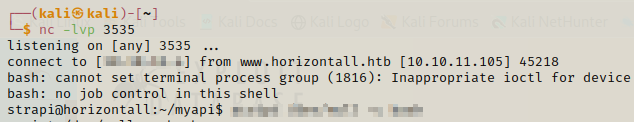
After we execute the exploit ,we need to make sure we have a netcat listener open in another terminal and then run the bash command to get the shell.
We got the shell as strapi and we can easily get the flag from user.txt but we need to think about privilege escalation.
Running the linpeas on the target can maybe take us somewhere but we need to transfer the linpeas file to do so. Another way would be to use basic commands like netstat.
The port 8000 here is interesting for us. But we don’t have direct access to it so port forwarding can be helpful. We have access to create a .ssh file .
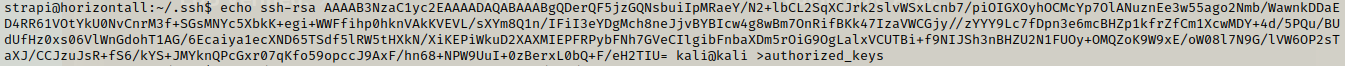
First we create a public key on our machine using ssh-keygen.
Now we just need to copy the key from strapi.pub and then create a .ssh folder in the strapi session and the in authorized_keys we can save it .
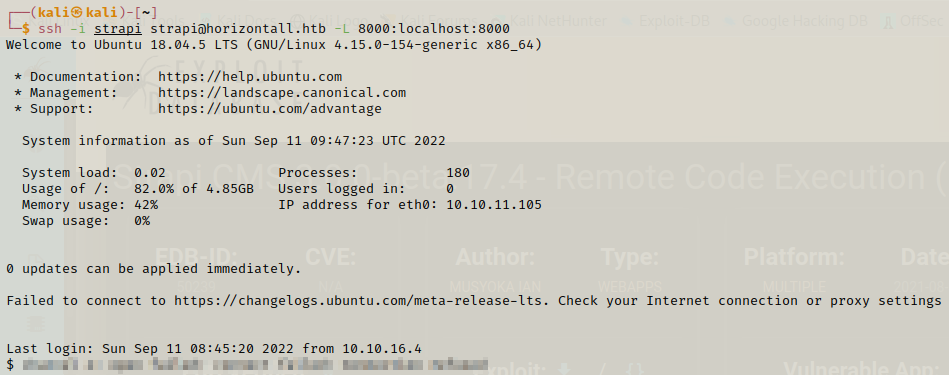
Now we can start ssh session using the strapi key we generated on our machine. We are also using local port forwarding with this session.
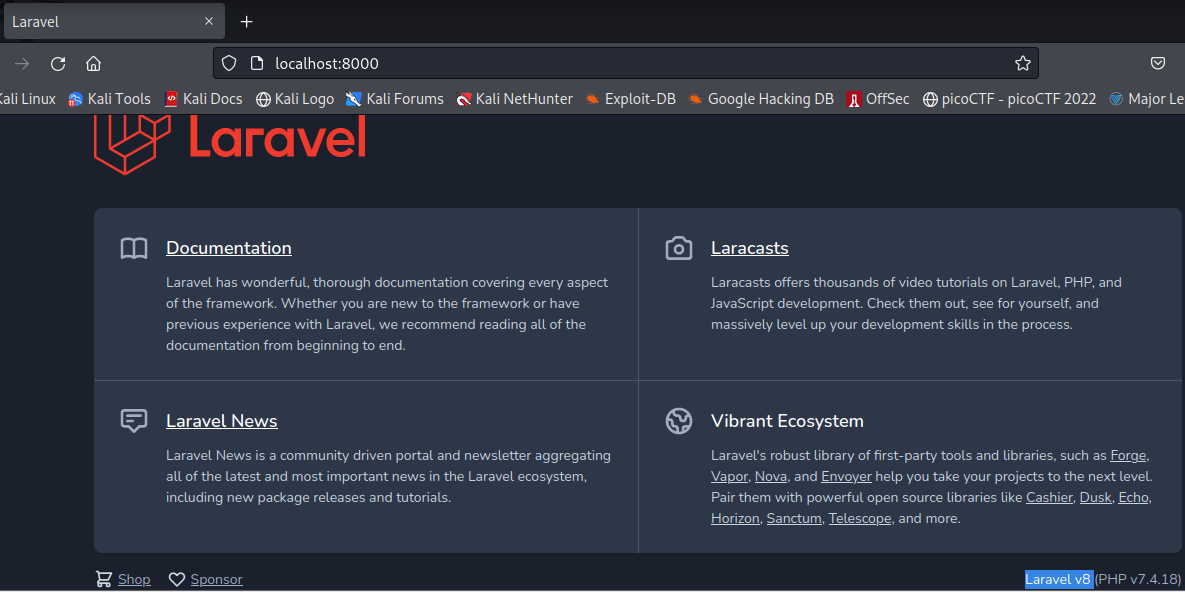
We can check if this is working by checking it through our browser.
We found that Laravel v8 is running on this so we can search exploits for this and CVE-2021–3129 has an exploit available with POC which we can use. With this exploit we can simply cat the contents of root.txt
We got our flag. Although this exploit can be used to get a reverse shell as well. Happy Hacking!!!!







Comments
Post a Comment