Hack The Box:Lame(Linux)
The nmap scan had some obvious findings.
Since the nmap scan is pointing out CVE-2004–2687, we can do some research on it. The CVE-2004–2687 has an exploit and POC is given with it ,which we can easily use to get a shell as Daemon. First we need to download the exploit. After that we need to follow the format given in the comments to run the exploit. There was one issue running this exploit ,that the comments somehow were creating problem and they were to be removed before running the exploit but that varies from system to system.
We also need to make sure on our attacking machine we have a listener.
We run the exploit in one terminal window and open a listener on the other one to get a shell.
Since username is Daemon we need to work on privilege escalation. We can read the user.txt file in this session only and get the first flag but the root.txt file will not show the output.
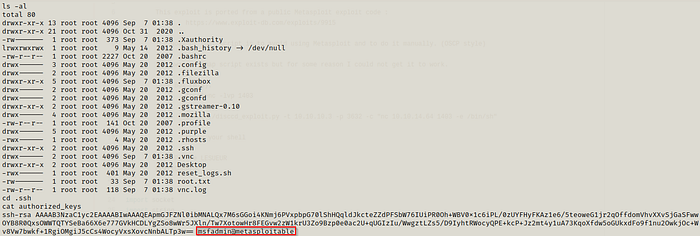
We try to find a way for privilege escalation and went to the .ssh folder, nothing useful as such but given that the key has msfadmin written that can be an indication that this key can be vulnerable to CVE-2008–0166, where the random number generator in OpenSSL broke for a period of time causing lots of thing, including some SSH keys, to be brute forcable from the public key.
This is actually a good information to learn if its new for you, there is g0tmi1k’s GitHub repo which is really good if we want to brute force the public key . We need to clone it and then unpack the common keys.
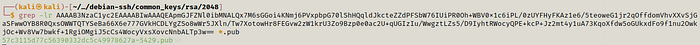
Now we can use grep -lr to find the filename with the public key.
After grep -lr it is the key we got from .ssh folder and we put a *.pub at the end to search for any file which might have this key.
Now that we got the file we use ssh and provide the file as key and we got root. After that we can search for root.txt to get the other flag.
This is one way of hacking this machine but there are others.Hope you learned something from this. Happy hacking!!!!




Comments
Post a Comment