Hack The Box:Buff(Windows)
The nmap scan for this machine shows two ports open.

We get a website on port 8080 ,but the login form of this one is not vulnerable to sql injection.

This page does reveal that its using gym management system and this has an exploit available on searchsploit.

We can use this exploit simply and specify the target. But we get access to the web shell not the system so we can’t do much here and need to get a reverse shell on our machine.

From here we can get the user flag.

From our machine we send the netcat exe file and then use it to get a reverse shell on our system but we need to make sure we have a listener on our machine.

We get an interactive shell on our machine which we can enumerate for priv esc.

When we enumerate we find out that there a port 8888 open on this machine internally .

After further enumeration we find that there is CloudMe_1112.exe file which is running on this port.

This CloudMe has a buffer overflow vulnerability which is available on searchsploit.
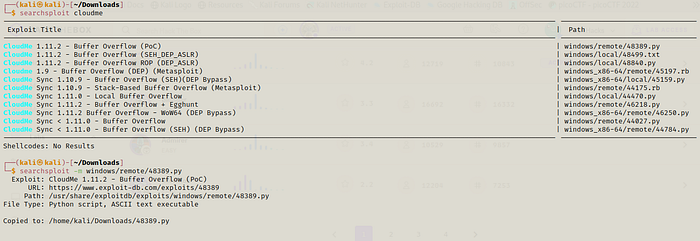
But to execute this we need to tunnel so we will use chisel. We will make our system a server and the target a client. On our machine we do this:

Now we need to transfer the chisel’s exe file and run a client .

We established a connected which we can confirm on our machine.

Now we just need to generate payload and replace it in the script.

Then we just run the script but we need to make sure we have netcat listener on our machine.

We get the shell as administrator and we get the root flag.

Happy hacking!!!!
Comments
Post a Comment