Hack The Box:Doctor(Linux)
We will start our journey with an nmap scan.

With the nmap scan we can understand there is splunk and the other thing is we have a web page .

When we access the web page it doesn’t have anything special to exploit. But we get to know about doctors.htb which is also a web page tied with this machine. To accesss it we need to modify the /etc/hosts file and add doctors.htb with ip address 10.10.10.209 .
We start with directory busting of this address.
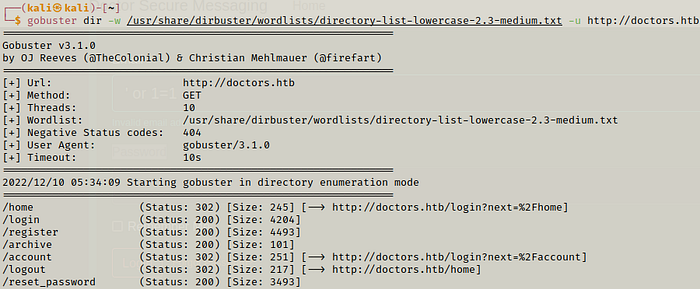
There is an interesting directory named login. We see a login page there but nothing works over there.

So we register a user which we can easily do.

Now if we login we get to see the home page with new message option.

If we type a message and see it in the archive page we get something like this.


So basically if we want we can send a command for reverse shell and using the archive page we can run it.
There are different types of server-side templates available but we need to check which one applies for this because this one has SSTI vulnerability. When we write in the title it gets reflected in the archive page.
We can check for SSTI by writing in the title field {5*5} -> {{5*5}} -> {{5*’5'}} -> Result 55555. This one is Jinja2.

We try to get a reverse shell using the command and that works. We just need to go to the 10.10.10.209/archive page and make sure we have a listener working on our machine.

There is a folder named backup which might be interesting for us.

We try to see if there is any password in this file using grep.

There is another user named shaun we can use this password with that user.

Now there is splunk and we can use tool for splunk to get shell as root.We need a listener on our machine and then we just need to run the tool.

We got the shell and the root flag.

Happy Hacking!!!!
Comments
Post a Comment